How to use the sudoers file to grant superuser privileges in Linux
In a Linux system there are tasks that need to be performed using administrative privileges (also known as superuser permissions) as they either impact the system as a whole (for example, managing packages or restarting services) or other users (adding or modifying user accounts, changing passwords or other users). Another example of a task requiring superuser privileges consists of changing the ownership or permissions of files and directories.
To perform this kind of work, a system administrator needs to gain temporary access to the root account or use the sudo command with his / her regular user account, provided that such account has been previously given the appropriate permissions in the /etc/sudoers file. In this article we will discuss how to edit this file in order to give certain user accounts the necessary privileges to perform administrative tasks in our system.
Configuring visudo to use your preferred text editor
Using /etc/sudoers, a system administrator can control the commands a user can run impersonating other users. This file is well-commented and is basically composed of variables (known as aliases) and other user specifications.
Although /etc/sudoers is a plain text file, it is strongly recommended that it is not edited by invoking a regular text editor such as nano or vim. In other words, DO NOT DO THIS:
vim /etc/sudoers
or
nano /etc/sudoers
The problem with the above approach is that it does not prevent two separate persons from editing the file. If, inadvertently, two or more people open the file for edition one of them may overwrite the changes made by other. Thus, the recommended way of editing /etc/sudoers consists of invoking the visudo command, which will open the file using the default text editor, which often is vi if the EDITOR environment variable has not been set. If you prefer to use nano instead, do:
EDITOR=/bin/nano export $EDITOR
Please note that this will make nano your default editor only during the current session. To set it permanently, add the two lines above to your .bash_profile and source it to apply changes immediately:
echo "EDITOR=/bin/nano" >> ~/.bash_profile echo "export EDITOR" >> ~/.bash_profile . ~/.bash_profile # Note there is a dot before path to the file!
That said, you will now be able to use either vi or nano to edit /etc/sudoers when you invoke visudo in the command line. When someone is using visudo to edit this file, other people will NOT be able to do the same, and will get the following error if he or she attempts to do it, as we can see in Fig. 1:
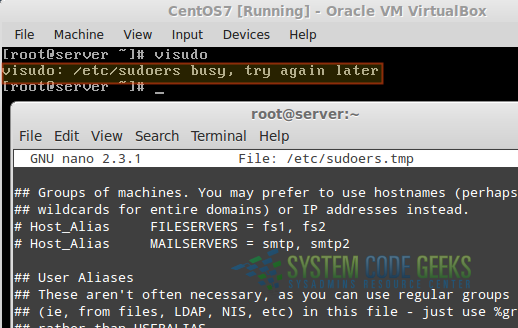
That said, let’s dive into /etc/sudoers with visudo.
Using visudo to edit /etc/sudoers and introducing aliases
After invoking visudo from the command line, the file will be opened using the text editor you chose previously. Let’s begin by taking a look at aliases, which allow us to set more convenient names for groups of hosts, users, and commands. Thus, you can use an alias to define a group and use the alias name to refer to it afterwards instead of naming each host, user, or command separately.
Host aliases are used to specify groups of hosts. The following line in /etc/sudoers indicates that when we use FILESERVERS we are actually referring to hosts fs1 AND fs2.
Host_Alias FILESERVERS = fs1, fs2
The following user alias specify that gacanepa AND scg can be referred to as ADMINS in the file.
User_Alias ADMINS = gacanepa, scg
If instead we want to allow ALL users to be part of ADMINS except for the ones mentioned above, we would do
User_Alias ADMINS = ALL, !gacanepa, !scg
The exclamation sign, when used as a prefix for an object in an alias, explicitly eliminates it from the specified group.
Finally, you can create as many command aliases as you need to reference related group of commands.
Cmnd_Alias SOFTWARE = /bin/rpm, /usr/bin/yum Cmnd_Alias STORAGE = /sbin/fdisk, /sbin/parted
The first line above (SOFTWARE) indicates that we can refer to rpm and yum as SOFTWARE, whereas the second specifies that STORAGE is a placeholder for fdisk and parted.
Granting permissions through user specifications
With the above aliases in place we are ready to add or edit user specifications. Particularly, we will use SOFTWARE and STORAGE in order to give users gacanepa and scg permissions to run the commands specified in those variables. To do that, let’s add the following line to /etc/sudoers:
ADMINS ALL=(root) SOFTWARE, STORAGE
The above line specifies that members of the ADMINS User_Alias (who) can run, on ALL hosts (where) as root (as who), the commands listed in the indicated Cmnd_Alias(es).
In other words, we can infer that the basic syntax of a user specification in /etc/sudoers is:
WHO WHERE=(AS WHO) WHAT
To indicate the WHO using regular Linux groups, we need to use a % sign followed by the group name. Other than that, the syntax is identical to the previous example. To illustrate, let’s give members of group developers permissions to run updatedb as root. By using the NOPASSWD tag, we will allow them to run that command without entering their password (note that it is not necessary to specify the AS WHO here as no password will be required)::
%developers ALL=NOPASSWD:/usr/bin/updatedb
Once you have finished editing /etc/sudoers, save changes and run visudo -c to check the configuration file for errors. If no errors are found, you will get the message shown in the left of Fig. 2, whereas if something is wrong, you will be prompted to make the necessary corrections in the indicated line (as shown in the middle and right of Fig. 2).
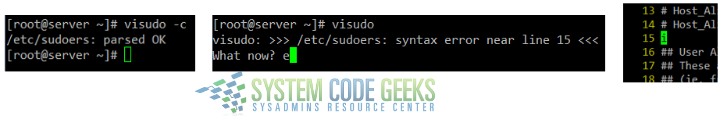
/etc/sudoers and correcting errors where foundAfter you have fixed the errors found, members of the developers group will be able to execute updatedb without password. Additionally, if a particular member of the developers group is logged on while you are making these changes, he or she will need to log out and log back in to see the changes.
Summary
In this article we have explained how to properly edit the /etc/sudoers file in order to grant superuser privileges to users and groups. This will allow them to run commands and perform tasks that require root permissions without giving them access to the root account.



